IEEE Victoris 2023 CTF - VulnPass
This is a writeup for the memory forensics challenge VulnPass authored for the IEEE Victoris CTF 2023 competition, organized by IEEE ManSB in partnership with EG-CERT.
Challenge Description
During first response on an APT group devices we were trying to access the C2 login dashboard and take down there infrastructure but failed to decrypt the browser credentials. Fortunately, we got this acquisition so you may help to access the dashboard!
Challenge file: VulnPass_MemDump.mem
Challenge Idea
In KeePass 2.x before 2.54, it is possible to recover the cleartext master password from a memory dump (CVE-2023-32784), After extracting the master password the database file (database2.kdbx) can be dumped from the memory. By using the recovered master key password to open the database, the flag can be obtained
Challenge Writeup
First, the memory profile was obtained using the imageinfo Volatility plugin.
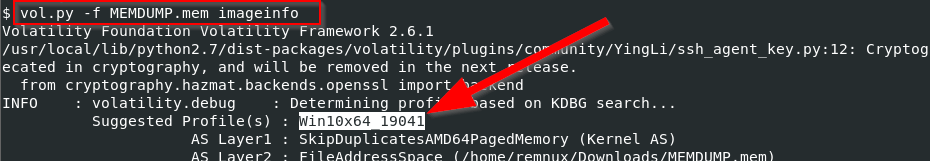
Then, the running processes were checked using the pslist plugin.
$ vol.py -f MEMDUMP.mem --profile=Win10x64_19041 pslist
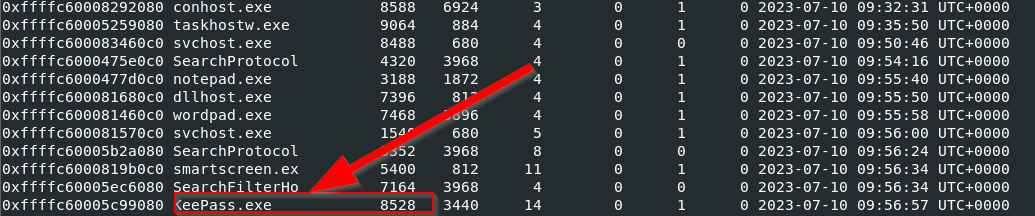
Among the interesting processes identified was KeePass.exe which is the keepass password manager application.
From the challenge description and name too we understand we are looking for credentials to access a login page, so let’s focus on the keepass application.
A quick search for how to extract the keepass passwords via a memory dump, revealed that KeePass has a known CVE (CVE-2023-32784) and it is possible to recover the cleartext master password from a memory dump. Running the poc
, the master key password was retrieved:
S3cr3tP4ss123
(Note: The first character was not recoverable but suggested, however the rest of the password made it possible to figure out the full key.)

With the password in hand, the next step was to locate the KeePass database file. The database file extension .kdbx, was identified through research, and a search for the file in the memory dump was performed using the filescan plugin.
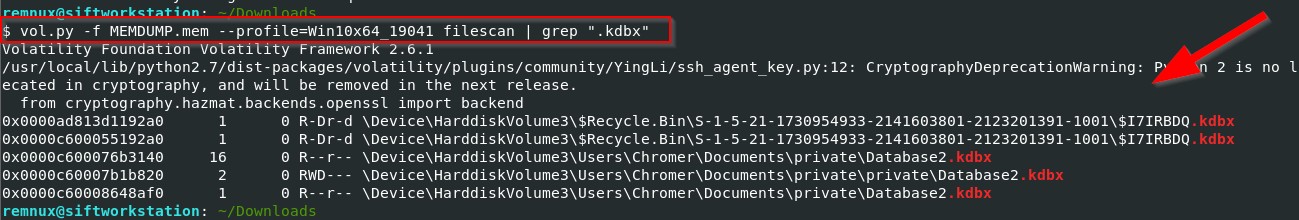
One of the database files was found and its address was noted. Since the machine in question was running Windows 10, the file’s address needed to be converted into a physical address using volshell. The resulting physical address was 0x497c6140L.
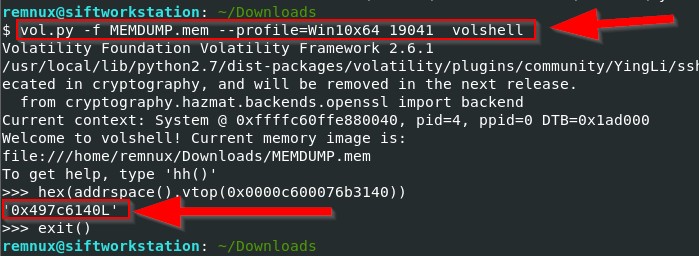
Using the dumpfiles plugin, the database file was successfully dumped.
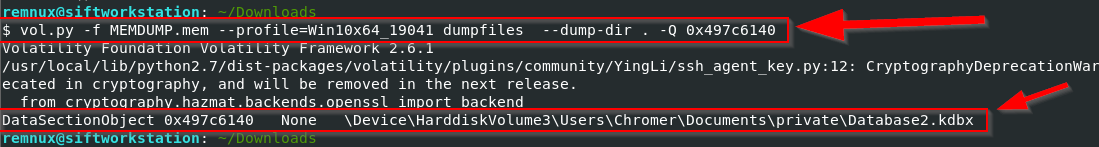
Opening the dumped database file in the KeePass application with the extracted password granted access to the database. Exploring the contents of the file, the flag was found in the second entry.
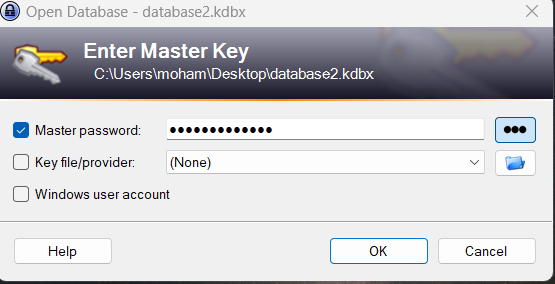
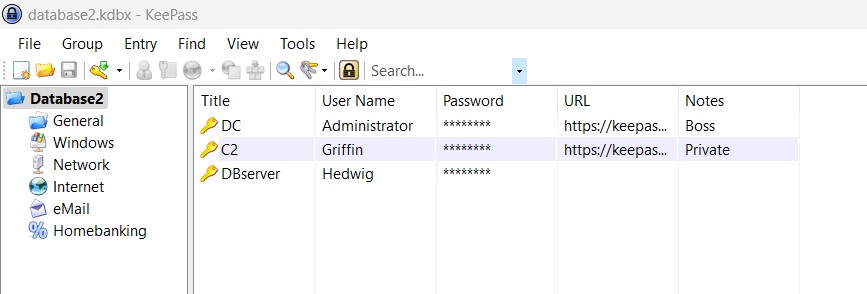
Flag :
EGCERT{10_P0ints_t0_Gryff1nd0r}
